Containers published by i-net software will run with a restricted user in their respective containers in early 2023. This is a major change and implies additional changes for existing containers.
Until now, containers were running with the user root. The default configuration and file persistence were stored in the container directory /root. Also, backup etc. was usually stored at this location.
Our updated containers will run with a restricted user with the UID and GID set to 1000. The name of the user depends on the product and can usually be resolved by $PRODUCT inside the container:
-
reporting- i-net Clear Reports -
pdfc- i-net PDFC -
helpdesk- i-net HelpDesk -
cowork- i-net CoWork
The user name can be derived from the call:
docker run inetsoftware/i-net-<PRODUCT>:<TAG> whoami
Data Migration
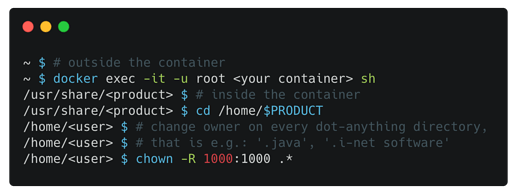
Due to the change of the service user, you’ll have to update the mount point into the container from /root to /home/$PRODUCT and update the file owner and group id to 1000:1000. This can best be achieved using the root user in the upgraded container:
Plain Bash Code
~ $ # outside the container
~ $ docker exec -it -u root <your container> sh
/usr/share/<product> $ # inside the container
/usr/share/<product> $ cd /home/$PRODUCT
/home/<user> $ # change owner on every dot-anything directory,
/home/<user> $ # that is e.g.: '.java', '.i-net software'
/home/<user> $ chown -R 1000:1000 .*
Custom Image Migration
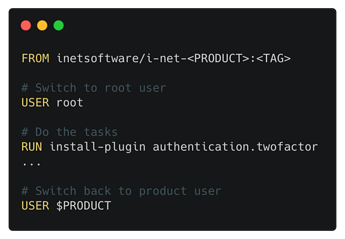
If you were using a custom image, built from one of our existing images, you’ll have to switch the user prior to installing any new software components to root and switch back to $PRODUCT when the operation is finished. Also, please make sure that any additionally installed components are available to the restricted service user, i.e. file permissions.
Plain Dockerfile
FROM inetsoftware/i-net-<PRODUCT>:<TAG>
# Switch to root user
USER root
# Do the tasks
RUN install-plugin authentication.twofactor
...
# Switch back to product user
USER $PRODUCT
Non-file persistence
(Update 2023-02-14: Containers build after this date do not have this restriction anymore)
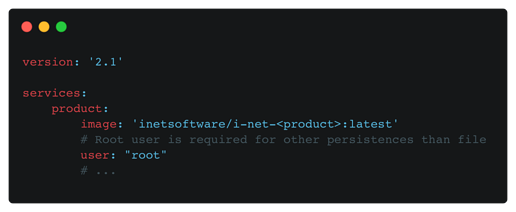
If you are using a non-file persistence, such as MongoDB, you will have to see using the root user for now. The reason for that is that the non-file persistences require the System-Scope for the configuration, which can otherwise not be used by the application.
To achieve the root-user context you can either create a custom image, without switching back to the product user or a docker compose file, which switches the runtime user to root:
Docker compse file
version: '2.1'
services:
product:
image: 'inetsoftware/i-net-<product>:latest'
# Root user is required for other persistences than file
user: "root"
# ...